Internet Safety Series: Protect your accounts with Two-Factor Authentication

Privacy. A requirement in the modern age of virtual work and interaction. Every day, passwords are stolen, seemingly secure databases are breached, and scam artists try to take what they can from your virtual sphere of what makes you, YOU.
We often get so blinded by the attractiveness and convenience of the technology available to us, that we overlook the underlying preventable issues simply because- “it’s seems like too much work”.
So, starting this week, we’re putting together a handy list of articles for you to keep yourself as safe as possible in this online world. These range from “how to lock down your Facebook”, all the way to “how to keep yourself secure on messaging platform”. Read on to learn more!
What is Two-Factor Authentication?
Today we’re talking about Two-Factor Authentication. Popularly known as 2FA, this is a service that allows the websites you visit, a secondary access to yourself to make sure that it really IS you. These can take several forms depending on your website or application. It can either use something called “Face-ID” that scans your face as part of the authentication or prompt you to type in your phone’s passcode, or your secondary email. It can also confirm your identity by asking you to scan your thumbprint on your phone’s sensor.
Two factor authentication is essential to web security because it reduces the risks associated with compromised passwords of your accounts. Strategies like hacking, guessing, and phishing are now less viable and are no longer enough to give an intruder or a bad agent access to your account; without approval of the second factor, a password alone is useless!
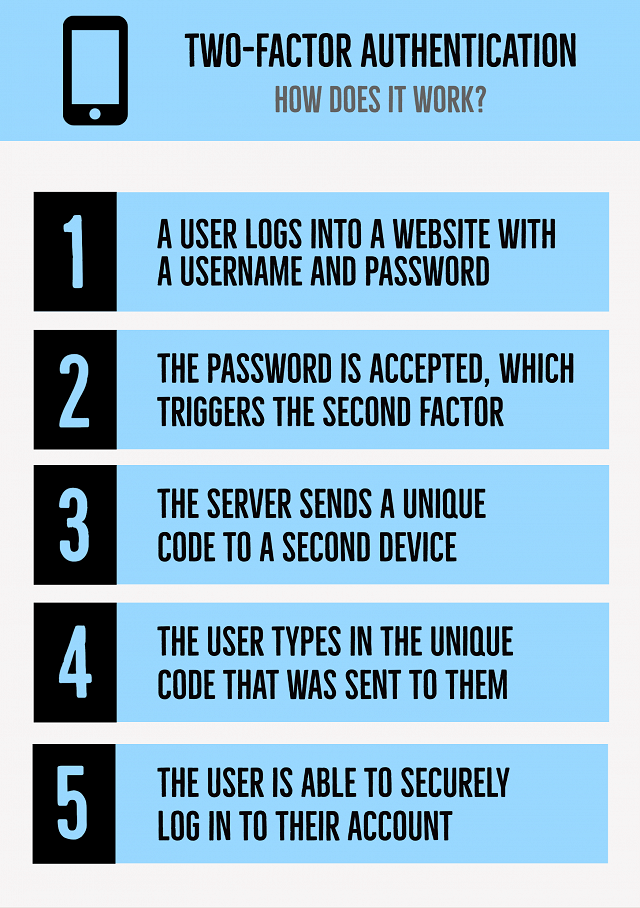 How does it actually work?
How does it actually work?
As mentioned previously, the two-factor authentication can take various forms, but the basic principle for this process, remains largely the same:
- As a first step, the user logs in to the website or service of their choice with their regular username and password that they created
- Once the correct credentials are typed in, the password is validated and accepted by an authentication server (if correct) and the user becomes eligible for the second factor.
- The authentication server then prompts the user and sends a unique code to the user’s second-factor device. (Another phone/tablet/laptop/pc of their choosing)
- The user confirms their identity by approving the additional authentication from their second-factor device by typing in the code that was sent to them. (Can be numerical or Alpha-numerical)
- The user then gains secure access to their account, and is able to sign-in.
How to set-up Two-Factor authentication on your Google Account:
- Open your Google Account.
- In the navigation panel, select Security.
- Under “Signing into Google,” select 2-Step Verification and then Get started.
- Follow the on-screen steps.
- If your account, username@gmail.com, is associated with your work or school and you can’t set up 2-Step Verification, you may have to contact your administrator or IT lead
How to set-up Two-Factor authentication on your Twitter Account:
- In the side menu, click More, then click Settings and privacy.
- Click on Security and account access, and then click Security.
- Click Two-factor authentication.
- There are three methods to choose from: Text message, Authentication app, or Security key.
- Choose “text” Message
- Follow the on-screen instructions
- Once enrolled, when you log in to your account, you'll be prompted to provide the two-factor authentication method you used during your previous login, along with your password. You’ll also see the option to Choose a different two-factor authentication method. If you’d like to proceed, simply click the prompt to select a different method. Follow the onscreen instructions to finish logging in.
While two-factor authentication might feel a bit overwhelming to set-up, it is an extremely important privacy tool! Make sure to never skimp on it, and enable it wherever possible! Stay safe out there!
